GoodAccess Essential Plan
Dedicated Cloud VPN with Static IP whitelisting Minimum of 5 users 1 Dedicated Gateway
GoodAccess Premium Plan
- ZTNA - Zero Trust Network Architecture for multi-site & cloud businesses (SSE / SDP / ZTNA) -Minimum of 5 users 1 Dedicated -Gateway 1 Cloud/Branch Connector
Enterprise
Enterprise features and Premium 24/7 support for large organizations On Request Minimum 50 users
Add-On
GoodAccess Dedicated Gateway
Optimize network performance for your global teams. Ensure high ….
GoodAccess Cloud/Branch Connector
Extend your secure network to more locations. Add extra connectors for ...
What you get with GoodAccess
Dedicated Cloud VPN
Dedicated VPN gateway
Choose a dedicated VPN gateway from locations all around the world in the blink of an eye. Virtual private infrastructure, secure web access, firewall, access control, and authentication service included.

WHITELIST YOUR STATIC IP
Static IP for IP whitelisting
Whitelist your public static IP to cloak your systems on the public internet so that only authorized users can access.

Split tunneling
Split tunneling
Through the GoodAccess dedicated VPN gateway you can easily control access to your critical systems and decide which traffic to route directly.

GoodAccess apps
Mobile and desktop apps
It takes only one click to connect from Windows, iOS, Mac, Android, and ChromeOS devices thanks to the native GoodAccess apps.

Secure shield
Secure encryption
GoodAccess creates an eavesdropping-resistant VPN tunnel via IKEv2/IPSec and OpenVPN protocols. Both are fast, designed to use unbroken ciphers and algorithms, and are equipped with features that keep the communication unreadable for bad actors.

2FA
Two-factor authentication
Harden your security controls by enforcing two-factor authentication (2FA) for the login to the GoodAccess management interface, client apps, and optionally for each connection.

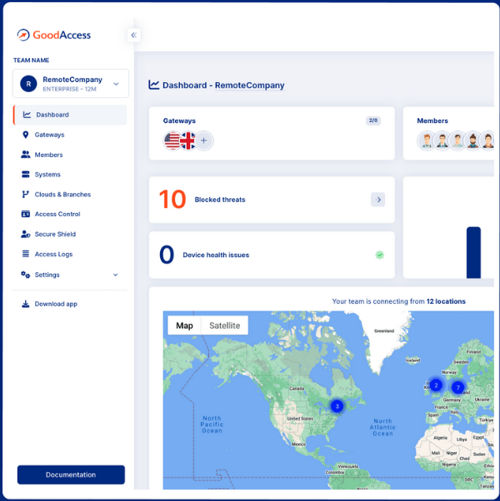
GOODACCESS DASHBOARD
Control panel
Add systems, apps, and devices into your network in a few clicks. Web interface with walkthroughs and user guides is optimized for easy network and user management and traffic visibility.

USER ACCESS LOGS
User activity logging
Maintain full control over gateway access points, allowing you to track and manage network connections with precision. This strengthens security, mitigates risks, and supports compliance with GDPR, SOC2, or HIPAA regulations.